Overview
Fortifying Security on Your Hybrid and Public Clouds
Public cloud environments present unique security challenges for applications and infrastructure. The inherently dynamic and ephemeral nature of cloud-native resources, such as containers and serverless functions, makes it difficult to consistently monitor, control access, and enforce policies. As a result, organizations struggle to effectively detect misconfigurations, unauthorized access, abnormal traffic behaviors, suspicious API calls, and other vulnerabilities and threats.
Business Benefits

Holistic Risk Management
Effectively automate asset discovery, dependency analysis, compliance posture management, and impact containment. Manage dynamic attack surfaces with hyper automation and ensure compliance in complex environments.
Timely Threat Detection
By applying Artificial Intelligence (AI) and Machine Learning (ML) technology to continuously analyze events, logs, traffic, authorization and authentication activities, we can quickly identify suspicious and abnormal behaviors.
Rapid Threat Response
Highly automated event triage, correlation, and AI-assisted analysis provides timely insights on actions needed for risk mitigation and incident response. Our solutions respond to cyber risks and incidents rapidly.
Secure Cloud Native Services
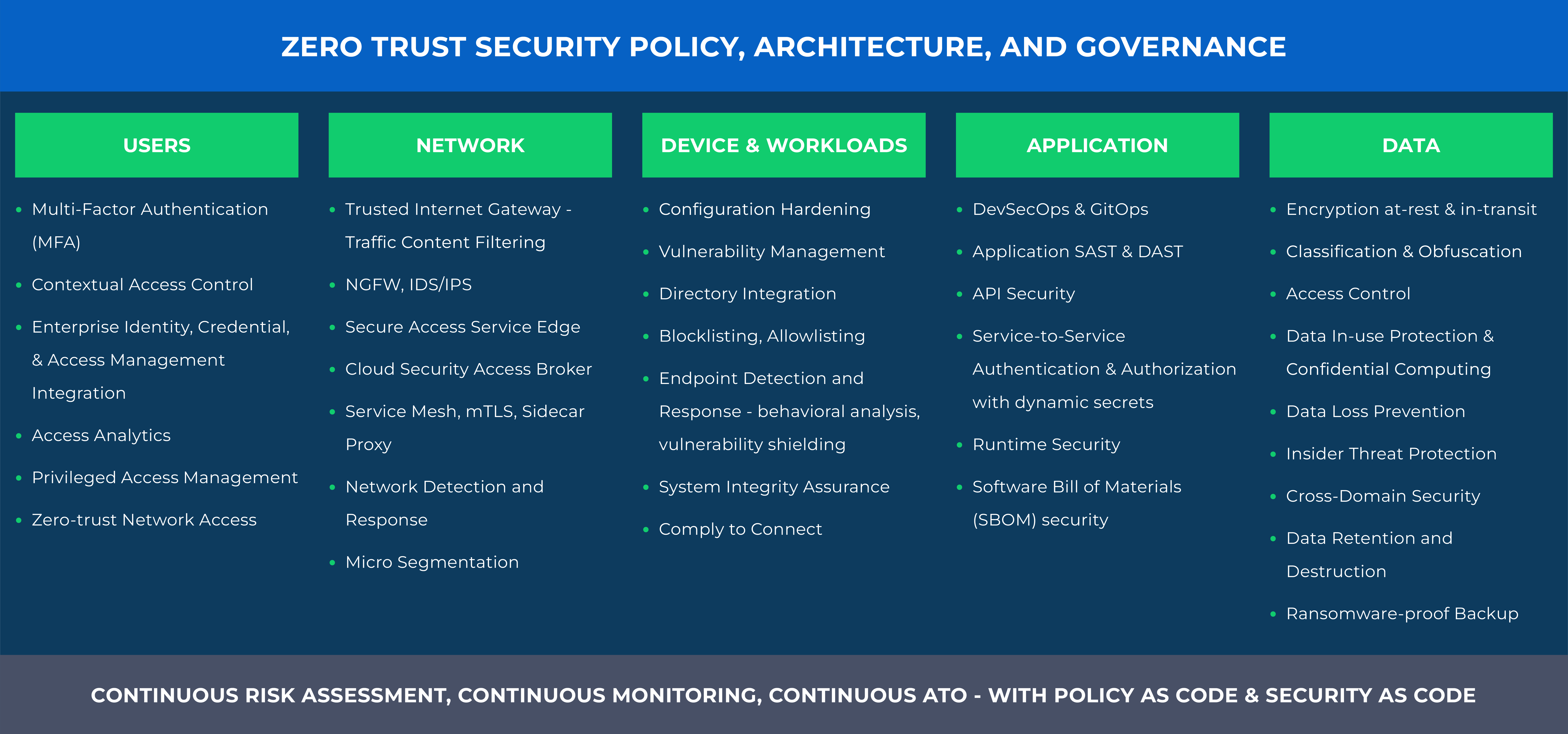
We apply a Zero-Trust security framework and a Development, Security, and Operations (DevSecOps) approach to manage the compliance and security of cloud-native services, including containers, Kubernetes, and serverless functions.
Support for Hybrid Cloud Environments
We provide compliance and security protection across on-premises systems and public clouds with a unified security management platform and dashboard.
Improved Security Posture
Continuously and consistently enforcing compliance policies with compliance -as-code enhances the overall security posture and reduces the risk of breaches or regulatory violations

FEATURES
Automated Security Posture Management
Our solution automatically discovers cloud assets, configurations, metadata, networking details, and configuration changes without an agent. By applying micro-segmentation capabilities, the solution contains security risks and manages security postures at a more granular level, minimizing the impact of a cyber breach.
Comprehensive Data Security Management
Our solution discovers sensitive data, automatically classifies data based on predefined policies, assesses data exposure risks, and prioritizes remediation to prevent data breaches. We provide rapid, agentless visibility into critical data stored in public and private buckets, data volumes, and hosted and managed databases, and apply proper data protection controls in accordance with data classification.
Automated Threat Detection and Response Orchestration
With continuous and unified visibility into identity privileges, resource access, asset behaviors, and network activities across cloud services -- Software as a Service (SaaS), Platform as a Service (PaaS), Infrastructure as a Service (IaaS), our solution detects, investigates, and responds to threats and security incidents in cloud environments autonomously.
Infrastructure as Code (IaC) Security
Applying the principle of DevSecOps, we use security scans to detect misconfigurations, exposed secrets, sensitive data, insecure defaults, open-source vulnerabilities, and container image vulnerabilities in IaC templates and scripts. We also scan for vulnerabilities within libraries and modules. Our IaC security approach centralizes security policy management across diverse cloud environments.
Cloud Identity and Entitlement Management
Our solution manages identities, entitlements, and access privileges across cloud and multi-cloud environments. It enforces least privilege access through permission discovery, detecting excessive or unused privileges and enabling rightsizing of entitlements.
Accelerated Cloud Security ATO
With Compliance-as-Code solutions, we automate security controls across cloud environments, manage security configurations and postures in a unified repository, and generate security accreditation documents with automation.

Model
Insights